The Complete Guide to Building HTML5 Games with Canvas & SVG:
After spending most of his time explaining to students, hobbyists, professional developers and teachers how to build games using HTML5, David thought to himself, rather than keeping all these details for small audiences, wouldn’t it be smarter to share it with you? This article is then based on his own experience in doing so and helping other to build HTML games with Canvas and SVG.
Monday, December 3, 2012
Monday, November 12, 2012
Is JavaScript the Future of Programming?
Is JavaScript the Future of Programming?:

JavaScript is the programming language that makes a website interactive. Slideshows, advertising pop-ups and Google's autocomplete feature are all examples of JavaScript at work. It was first created by Brendan Eich at Netscape in 1995 -- nicknamed Mocha during development, released in beta as LiveScript and ultimately named JavaScript in order to piggyback on the popularity of Java (another programming language) for marketing reasons.
At first, developers didn't take JavaScript seriously, because it wasn't seen as a serious development language like Java, Ruby or Python, which are server-side languages. JavaScript was the frosting on the cake, only responsible for user experience. B…
Continue reading...
More About: Ajax, Did You Know, features, front end, mashable, node.js, programming


JavaScript is the programming language that makes a website interactive. Slideshows, advertising pop-ups and Google's autocomplete feature are all examples of JavaScript at work. It was first created by Brendan Eich at Netscape in 1995 -- nicknamed Mocha during development, released in beta as LiveScript and ultimately named JavaScript in order to piggyback on the popularity of Java (another programming language) for marketing reasons.
At first, developers didn't take JavaScript seriously, because it wasn't seen as a serious development language like Java, Ruby or Python, which are server-side languages. JavaScript was the frosting on the cake, only responsible for user experience. B…
Continue reading...
More About: Ajax, Did You Know, features, front end, mashable, node.js, programming
Thursday, November 1, 2012
Ten - oh, wait, eleven - Eleven things you should know about the ASP.NET Fall 2012 Update
Ten - oh, wait, eleven - Eleven things you should know about the ASP.NET Fall 2012 Update:
Today, just a little over two months after the big ASP.NET 4.5 / ASP.NET MVC 4 / ASP.NET Web API / Visual Studio 2012 / Web Matrix 2 release, the first preview of the ASP.NET Fall 2012 Update is out. Here's what you need to know:
If you create a new ASP.NET MVC application using one of the new templates, you'll see that it's using the ASP.NET MVC 4 RTM NuGet package (4.0.20710.0):
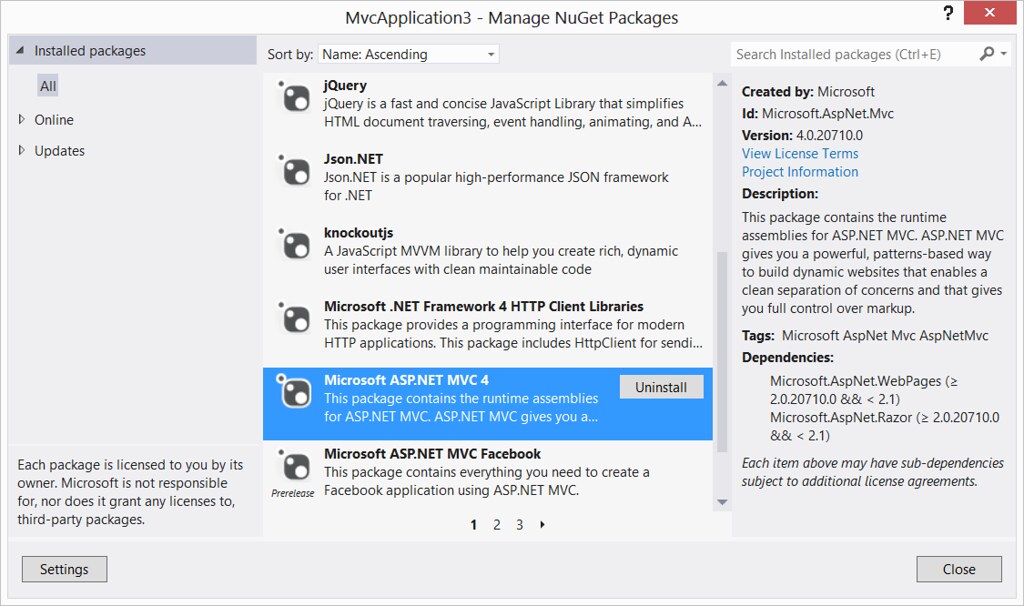
This means you can install and use the Fall Update without any impact on your existing projects and no worries about upgrading or compatibility.
You could create Facebook application in ASP.NET already, you'd just need to go through a few steps:
Erik Porter, Nathan and some other experts built out the Facebook Application template so it automatically pulls in and configures the Facebook NuGet package and makes it really easy to take advantage of it in an ASP.NET MVC application.
One great example is the the way you access a Facebook user's information. Take a look at the following code in a File / New / MVC / Facebook Application site. First, the Home Controller Index action:
First, notice that there's a FacebookAuthorize attribute which requires the user is authenticated via Facebook and requires permissions to access their e-mail address. It binds to two things: a custom MyAppUser object and a list of friends. Let's look at the MyAppUser code:
You can add in other custom fields if you want, but you can also just bind to a FacebookUser and it will automatically pull in the available fields. You can even just bind directly to a FacebookUser and check for what's available in debug mode, which makes it really easy to explore.
For more information and some walkthroughs on creating Facebook applications, see:
Early releases of ASP.NET MVC 4 included a Single Page Application template, but it was removed for the official release. There was a lot of interest in it, but it was kind of complex, as it handled features for things like data management. The new Single Page Application template that ships with the Fall Update is more lightweight. It uses Knockout.js on the client and ASP.NET Web API on the server, and it includes a sample application that shows how they all work together.
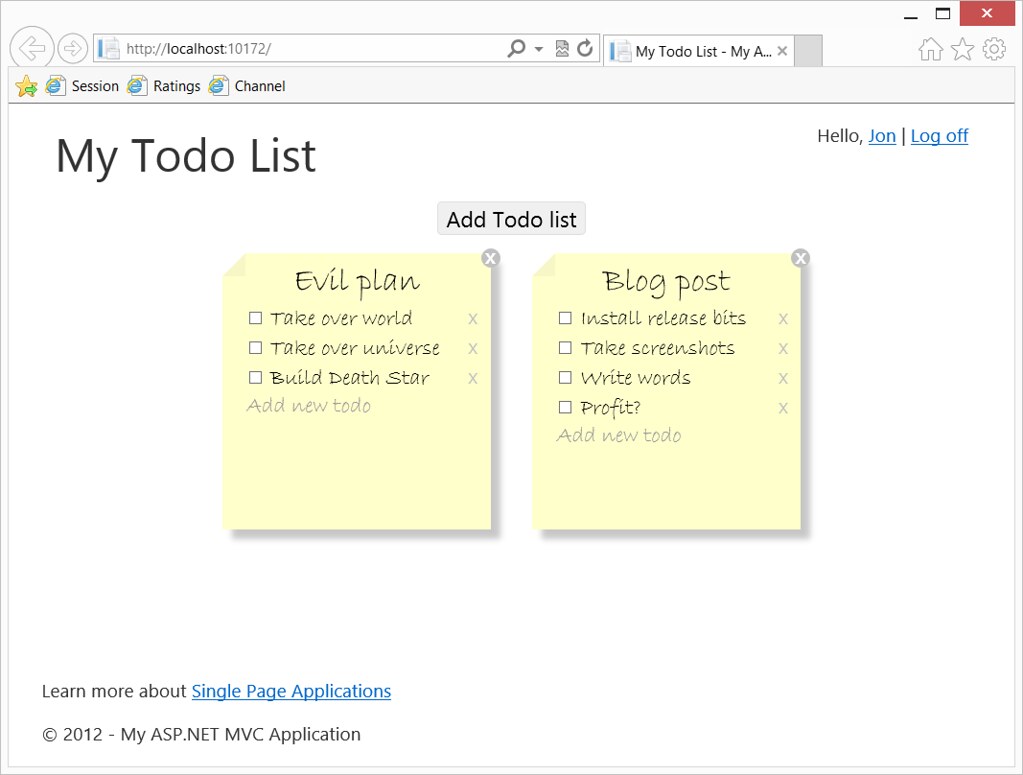
I think the real benefit of this application is that it shows a good pattern for using ASP.NET Web API and Knockout.js. For instance, it's easy to end up with a mess of JavaScript when you're building out a client-side application. This template uses three separate JavaScript files (delivered via a Bundle, of course):
This is a fun one to play with, because you can just create a new Single Page Application and hit F5.
One of the cool engineering changes for this release is a big update to the installer to make it more lightweight and efficient. I've been running nightly builds of this for a few weeks to prep for my BUILD demos, and the install has been really quick and easy to use. The install takes about 5 minutes, has never required a reboot for me, and the uninstall is just as simple.

There's one gotcha, though. In this preview release, you may hit an issue that will require you to uninstall and re-install the NuGet VSIX package. The problem comes up when you create a new MVC application and see this dialog:

The solution, as explained in the release notes, is to uninstall and re-install the NuGet VSIX package:
This took me under a minute to do, and I was up and running.
Uh, the Web API team is out of hand. They added a ton of new stuff: OData support, Tracing, and API Help Page generation.
Some people like OData. Some people start twitching when you mention it. If you're in the first group, this is for you. You can add a [Queryable] attribute to an API that returns an IQueryable<Whatever> and you get OData query support from your clients. Then, without any extra changes to your client or server code, your clients can send filters like this: /Suppliers?$filter=Name eq ‘Microsoft’
For more information about OData support in ASP.NET Web API, see Alex James' mega-post about it: OData support in ASP.NET Web API
Tracing makes it really easy to leverage the .NET Tracing system from within your ASP.NET Web API's. If you look at the \App_Start\WebApiConfig.cs file in new ASP.NET Web API project, you'll see a call to TraceConfig.Register(config). That calls into some code in the new \App_Start\TraceConfig.cs file:
As you can see, this is using the standard trace system, so you can extend it to any other trace listeners you'd like. To see how it works with the built in diagnostics trace writer, just run the application call some API's, and look at the Visual Studio Output window:
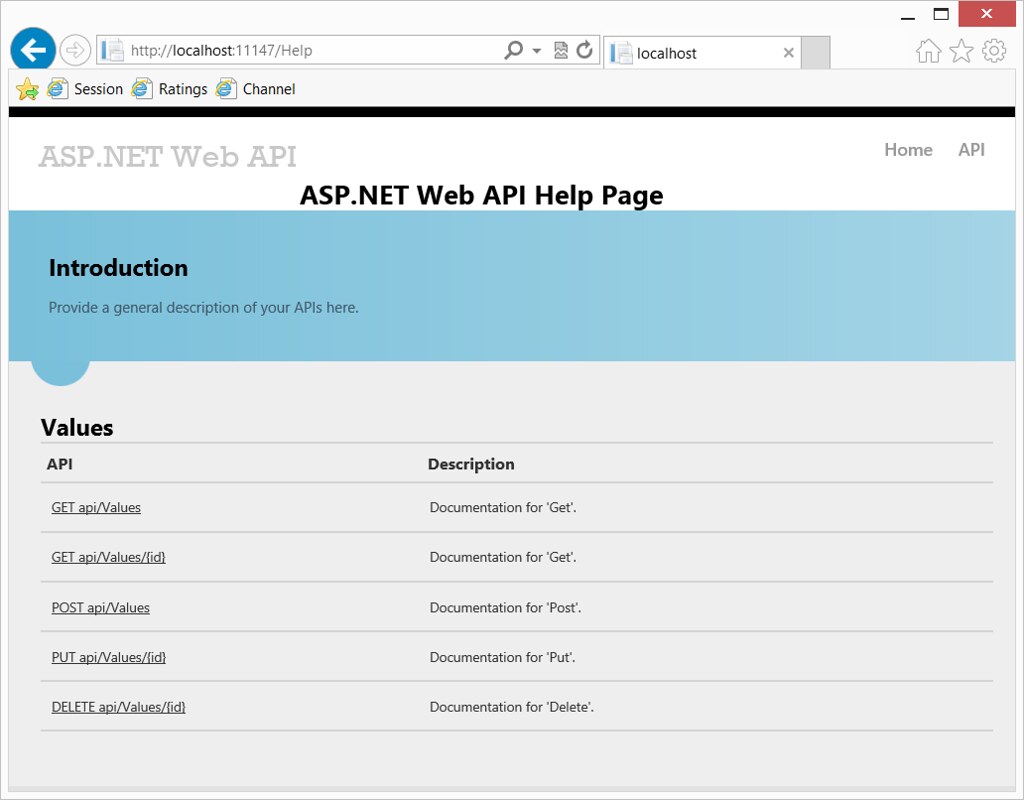
When you create a new ASP.NET Web API project, you'll see an API link in the header:
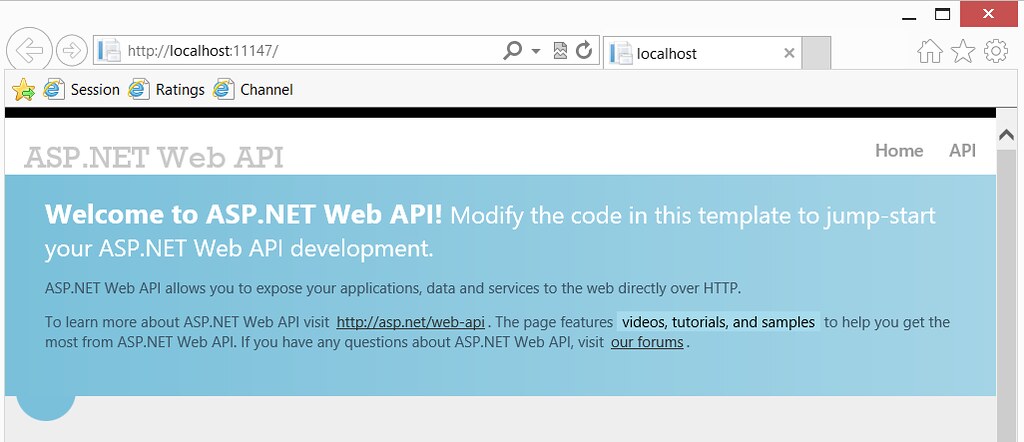
Clicking the API link shows generated help documentation for your ASP.NET Web API controllers:
And clicking on any of those APIs shows specific information:
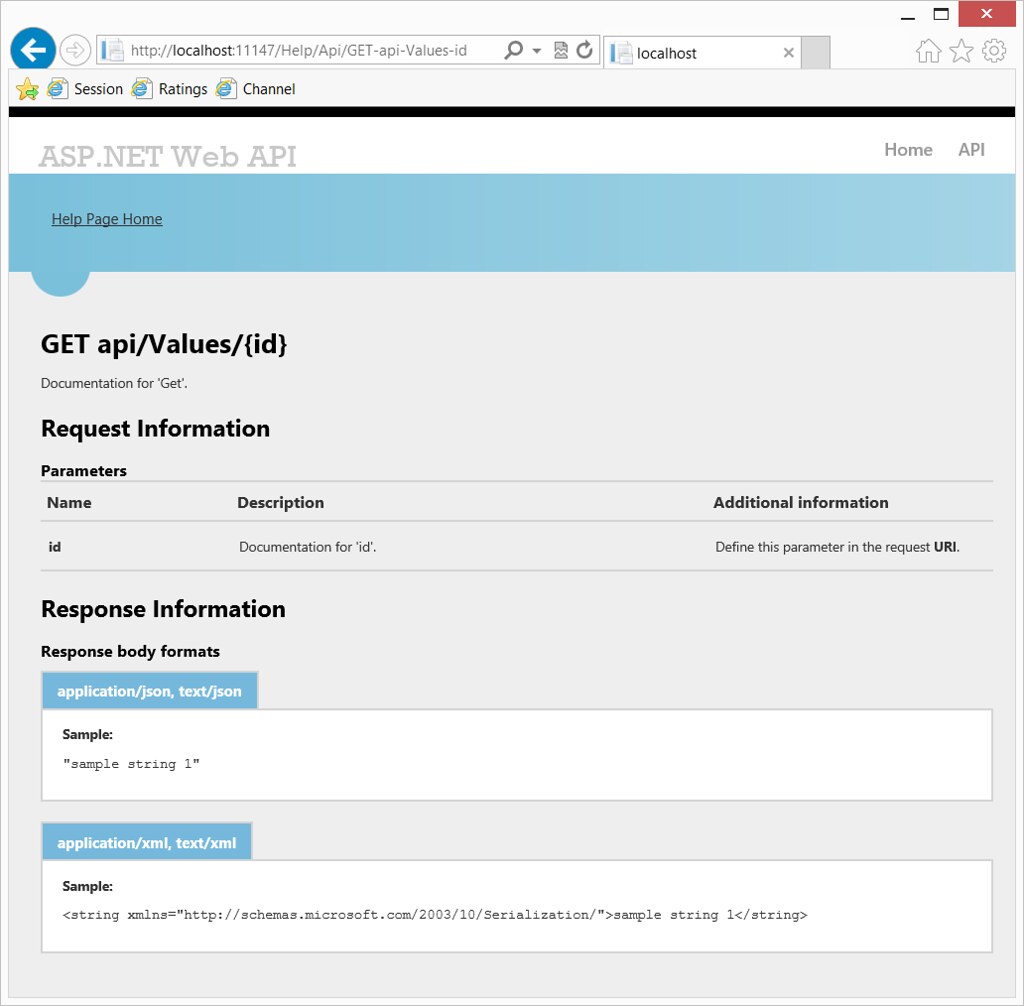
What's great is that this information is dynamically generated, so if you add your own new APIs it will automatically show useful and up to date help. This system is also completely extensible, so you can generate documentation in other formats or customize the HTML help as much as you'd like. The Help generation code is all included in an ASP.NET MVC Area:
SignalR is a really slick open source project that was started by some ASP.NET team members in their spare time to add real-time communications capabilities to ASP.NET - and .NET applications in general. It allows you to handle long running communications channels between your server and multiple connected clients using the best communications channel they can both support - websockets if available, falling back all the way to old technologies like long polling if necessary for old browsers.
SignalR remains an open source project, but now it's being included in ASP.NET (also open source, hooray!). That means there's real, official ASP.NET engineering work being put into SignalR, and it's even easier to use in an ASP.NET application. Now in any ASP.NET project type, you can right-click / Add / New Item... SignalR Hub or Persistent Connection.

There's quite a bit more. You can find more info at http://asp.net/vnext, and we'll be adding more content as fast as we can. Watch my BUILD talk to see as I demonstrate these and other features in the ASP.NET Fall 2012 Update, as well as some other even futurey-er stuff!


Today, just a little over two months after the big ASP.NET 4.5 / ASP.NET MVC 4 / ASP.NET Web API / Visual Studio 2012 / Web Matrix 2 release, the first preview of the ASP.NET Fall 2012 Update is out. Here's what you need to know:
- There are no new framework bits in this release - there's no change or update to ASP.NET Core, ASP.NET MVC or Web Forms features. This means that you can start using it without any updates to your server, upgrade concerns, etc.
- This update is really an update to the project templates and Visual Studio tooling, conceptually similar to the ASP.NET MVC 3 Tools Update.
- It's a relatively lightweight install. It's a 41MB download. I've installed it many times and usually takes 5-7 minutes; it's never required a reboot.
- It adds some new project templates to ASP.NET MVC: Facebook Application and Single Page Application templates.
- It adds a lot of cool enhancements to ASP.NET Web API.
- It adds some tooling that makes it easy to take advantage of features like SignalR, Friendly URLs, and Windows Azure Authentication.
- Most of the new features are installed via NuGet packages.
- Since ASP.NET is open source, nightly NuGet packages are available, and the roadmap is published, most of this has really been publicly available for a while.
- The official name of this drop is the ASP.NET Fall 2012 Update BUILD Prerelease. Please do not attempt to say that ten times fast. While the EULA doesn't prohibit it, it WILL legally change your first name to Scott.
- As with all new releases, you can find out everything you need to know about the Fall Update at http://asp.net/vnext (especially the release notes!)
- I'm going to be showing all of this off, assisted by special guest code monkey Scott Hanselman, this Friday at BUILD: Bleeding edge ASP.NET: See what is next for MVC, Web API, SignalR and more… (and I've heard it will be livestreamed).
No new bits
ASP.NET 4.5, MVC 4 and Web API have a lot of great core features. I see the goal of this update release as making it easier to put those features to use to solve some useful scenarios by taking advantage of NuGet packages and template code.If you create a new ASP.NET MVC application using one of the new templates, you'll see that it's using the ASP.NET MVC 4 RTM NuGet package (4.0.20710.0):

This means you can install and use the Fall Update without any impact on your existing projects and no worries about upgrading or compatibility.
New Facebook Application Template
ASP.NET MVC 4 (and ASP.NET 4.5 Web Forms) included the ability to authenticate your users via OAuth and OpenID, so you could let users log in to your site using a Facebook account. One of the new changes in the Fall Update is a new template that makes it really easy to create full Facebook applications.
You could create Facebook application in ASP.NET already, you'd just need to go through a few steps:
- Search around to find a good Facebook NuGet package, like the Facebook C# SDK (written by my friend Nathan Totten and some other Facebook SDK brainiacs).
- Read the Facebook developer documentation to figure out how to authenticate and integrate with them.
- Write some code, debug it and repeat until you got something working.
- Get started with the application you'd originally wanted to write.
Erik Porter, Nathan and some other experts built out the Facebook Application template so it automatically pulls in and configures the Facebook NuGet package and makes it really easy to take advantage of it in an ASP.NET MVC application.
One great example is the the way you access a Facebook user's information. Take a look at the following code in a File / New / MVC / Facebook Application site. First, the Home Controller Index action:
[FacebookAuthorize(Permissions = "email")]
public ActionResult Index(MyAppUser user, FacebookObjectList<MyAppUserFriend> userFriends)
{
ViewBag.Message = "Modify this template to jump-start your Facebook application using ASP.NET MVC.";
ViewBag.User = user;
ViewBag.Friends = userFriends.Take(5);
return View();
}First, notice that there's a FacebookAuthorize attribute which requires the user is authenticated via Facebook and requires permissions to access their e-mail address. It binds to two things: a custom MyAppUser object and a list of friends. Let's look at the MyAppUser code:
using Microsoft.AspNet.Mvc.Facebook.Attributes;
using Microsoft.AspNet.Mvc.Facebook.Models;
// Add any fields you want to be saved for each user and specify the field name in the JSON coming back from Facebook
// https://developers.facebook.com/docs/reference/api/user/
namespace MvcApplication3.Models
{
public class MyAppUser : FacebookUser
{
public string Name { get; set; }
[FacebookField(FieldName = "picture", JsonField = "picture.data.url")]
public string PictureUrl { get; set; }
public string Email { get; set; }
}
}You can add in other custom fields if you want, but you can also just bind to a FacebookUser and it will automatically pull in the available fields. You can even just bind directly to a FacebookUser and check for what's available in debug mode, which makes it really easy to explore.
For more information and some walkthroughs on creating Facebook applications, see:
Deploying your first Facebook App on Azure using ASP.NET MVC Facebook Template (Yao Huang Lin)
Facebook Application Template Tutorial (Erik Porter)
Single Page Application template
Early releases of ASP.NET MVC 4 included a Single Page Application template, but it was removed for the official release. There was a lot of interest in it, but it was kind of complex, as it handled features for things like data management. The new Single Page Application template that ships with the Fall Update is more lightweight. It uses Knockout.js on the client and ASP.NET Web API on the server, and it includes a sample application that shows how they all work together.

I think the real benefit of this application is that it shows a good pattern for using ASP.NET Web API and Knockout.js. For instance, it's easy to end up with a mess of JavaScript when you're building out a client-side application. This template uses three separate JavaScript files (delivered via a Bundle, of course):
- todoList.js - this is where the main client-side logic lives
- todoList.dataAccess.js - this defines how the client-side application interacts with the back-end services
- todoList.bindings.js - this is where you set up events and overrides for the Knockout bindings - for instance, hooking up jQuery validation and defining some client-side events
This is a fun one to play with, because you can just create a new Single Page Application and hit F5.
Quick, easy install (with one gotcha)
One of the cool engineering changes for this release is a big update to the installer to make it more lightweight and efficient. I've been running nightly builds of this for a few weeks to prep for my BUILD demos, and the install has been really quick and easy to use. The install takes about 5 minutes, has never required a reboot for me, and the uninstall is just as simple.

There's one gotcha, though. In this preview release, you may hit an issue that will require you to uninstall and re-install the NuGet VSIX package. The problem comes up when you create a new MVC application and see this dialog:

The solution, as explained in the release notes, is to uninstall and re-install the NuGet VSIX package:
- Start Visual Studio 2012 as an Administrator
- Go to Tools->Extensions and Updates and uninstall NuGet.
- Close Visual Studio
- Navigate to the ASP.NET Fall 2012 Update installation folder:
- For Visual Studio 2012: Program Files\Microsoft ASP.NET\ASP.NET Web Stack\Visual Studio 2012
- For Visual Studio 2012 Express for Web: Program Files\Microsoft ASP.NET\ASP.NET Web Stack\Visual Studio Express 2012 for Web
- Double click on the NuGet.Tools.vsix to reinstall NuGet
This took me under a minute to do, and I was up and running.
ASP.NET Web API Update Extravaganza!
Uh, the Web API team is out of hand. They added a ton of new stuff: OData support, Tracing, and API Help Page generation.
OData support
Some people like OData. Some people start twitching when you mention it. If you're in the first group, this is for you. You can add a [Queryable] attribute to an API that returns an IQueryable<Whatever> and you get OData query support from your clients. Then, without any extra changes to your client or server code, your clients can send filters like this: /Suppliers?$filter=Name eq ‘Microsoft’
For more information about OData support in ASP.NET Web API, see Alex James' mega-post about it: OData support in ASP.NET Web API
ASP.NET Web API Tracing
Tracing makes it really easy to leverage the .NET Tracing system from within your ASP.NET Web API's. If you look at the \App_Start\WebApiConfig.cs file in new ASP.NET Web API project, you'll see a call to TraceConfig.Register(config). That calls into some code in the new \App_Start\TraceConfig.cs file:
public static void Register(HttpConfiguration configuration)
{
if (configuration == null)
{
throw new ArgumentNullException("configuration");
}
SystemDiagnosticsTraceWriter traceWriter =
new SystemDiagnosticsTraceWriter()
{
MinimumLevel = TraceLevel.Info,
IsVerbose = false
};
configuration.Services.Replace(typeof(ITraceWriter), traceWriter);
}As you can see, this is using the standard trace system, so you can extend it to any other trace listeners you'd like. To see how it works with the built in diagnostics trace writer, just run the application call some API's, and look at the Visual Studio Output window:
iisexpress.exe Information: 0 : Request, Method=GET, Url=http://localhost:11147/api/Values, Message='http://localhost:11147/api/Values' iisexpress.exe Information: 0 : Message='Values', Operation=DefaultHttpControllerSelector.SelectController iisexpress.exe Information: 0 : Message='WebAPI.Controllers.ValuesController', Operation=DefaultHttpControllerActivator.Create iisexpress.exe Information: 0 : Message='WebAPI.Controllers.ValuesController', Operation=HttpControllerDescriptor.CreateController iisexpress.exe Information: 0 : Message='Selected action 'Get()'', Operation=ApiControllerActionSelector.SelectAction iisexpress.exe Information: 0 : Operation=HttpActionBinding.ExecuteBindingAsync iisexpress.exe Information: 0 : Operation=QueryableAttribute.ActionExecuting iisexpress.exe Information: 0 : Message='Action returned 'System.String[]'', Operation=ReflectedHttpActionDescriptor.ExecuteAsync iisexpress.exe Information: 0 : Message='Will use same 'JsonMediaTypeFormatter' formatter', Operation=JsonMediaTypeFormatter.GetPerRequestFormatterInstance iisexpress.exe Information: 0 : Message='Selected formatter='JsonMediaTypeFormatter', content-type='application/json; charset=utf-8'', Operation=DefaultContentNegotiator.Negotiate iisexpress.exe Information: 0 : Operation=ApiControllerActionInvoker.InvokeActionAsync, Status=200 (OK) iisexpress.exe Information: 0 : Operation=QueryableAttribute.ActionExecuted, Status=200 (OK) iisexpress.exe Information: 0 : Operation=ValuesController.ExecuteAsync, Status=200 (OK) iisexpress.exe Information: 0 : Response, Status=200 (OK), Method=GET, Url=http://localhost:11147/api/Values, Message='Content-type='application/json; charset=utf-8', content-length=unknown' iisexpress.exe Information: 0 : Operation=JsonMediaTypeFormatter.WriteToStreamAsync iisexpress.exe Information: 0 : Operation=ValuesController.Dispose
API Help Page
When you create a new ASP.NET Web API project, you'll see an API link in the header:

Clicking the API link shows generated help documentation for your ASP.NET Web API controllers:

And clicking on any of those APIs shows specific information:

What's great is that this information is dynamically generated, so if you add your own new APIs it will automatically show useful and up to date help. This system is also completely extensible, so you can generate documentation in other formats or customize the HTML help as much as you'd like. The Help generation code is all included in an ASP.NET MVC Area:

SignalR
SignalR is a really slick open source project that was started by some ASP.NET team members in their spare time to add real-time communications capabilities to ASP.NET - and .NET applications in general. It allows you to handle long running communications channels between your server and multiple connected clients using the best communications channel they can both support - websockets if available, falling back all the way to old technologies like long polling if necessary for old browsers.
SignalR remains an open source project, but now it's being included in ASP.NET (also open source, hooray!). That means there's real, official ASP.NET engineering work being put into SignalR, and it's even easier to use in an ASP.NET application. Now in any ASP.NET project type, you can right-click / Add / New Item... SignalR Hub or Persistent Connection.

And much more...
There's quite a bit more. You can find more info at http://asp.net/vnext, and we'll be adding more content as fast as we can. Watch my BUILD talk to see as I demonstrate these and other features in the ASP.NET Fall 2012 Update, as well as some other even futurey-er stuff!
Monday, October 8, 2012
The Truth About Structuring an HTML5 Page
The Truth About Structuring an HTML5 Page:
Part polemic, part instruction manual, The Truth About HTML5 has ignited an interesting debate. Here we present an exclusive excerpt on the problems around structuring in HTML5
Part polemic, part instruction manual, The Truth About HTML5 has ignited an interesting debate. Here we present an exclusive excerpt on the problems around structuring in HTML5
Saturday, June 2, 2012
Best method of learning Javascript?
Best method of learning Javascript?:
[link] [21 comments]
For some reason Javascript has been an extremely annoying language for me. I learned HTML and CSS without a hitch and I'm fairly decent with PHP. It seems like every book I read on Javascript never really goes in depth with how the syntax works and instead just gives you a bunch of examples. I'll get through a good chunk of a book and attempt to make even a simple script for a site...and have no idea whatsoever how. Anyone have any resources they maybe used to learn? Book Recommendations?
submitted by lordolunch [link] [21 comments]
Friday, June 1, 2012
Enterprise Resource Planning (ERP): What Are The Benefits Of Hosted/Cloud ERP Software
Enterprise Resource Planning (ERP): What Are The Benefits Of Hosted/Cloud ERP Software: Enterprise Resource Planning systems have changed a great deal over the years. Since cloud-based services have gained popularity, enterprise hosted solutions have had a high adoption rate. Although it is still a relatively new technology, cloud solutions are considered to be the way forward for enterprise resource planning (ERP) implementations. There are many advantages to [...]

.NET Performance Profiling: Learn the Skills, Write Better Code
.NET Performance Profiling: Learn the Skills, Write Better Code: In Practical Performance Profiling MVP Jean-Philippe explains how the .NET platform manages memory and uses a sample application based on a real software package to demonstrate a wide range of performance slowdowns
Monday, May 21, 2012
The Rapid Research Method
The Rapid Research Method:
The Rapid Research Method is a way to speed up your product research. It’s also a way to speed up ramp up time when you are leaning a new domain. The Rapid Research Method is also a key for rapid innovation and rapid product design and development. Lastly, the Rapid Research Method is also a great way to map out a space and perform competitive assessments.
One of the challenges with product development is doing effective research for your product design to make sure you have the right map of the pains and needs, the top concerns, and the key desired outcomes. Another challenge is actually making this information actionable and simple to share.
I’ve had the benefit of driving several projects end-to-end, so I’ve been through the research and exploration stage multiple times. I’ve learned a lot of tricks for speeding up research and making it more effective. I’ve had to use these techniques to play catch up in various domains from application architecture to security and performance, to even the cloud. They work.
I’m going to share a few techniques in this post. Collectively, I”ll refer to using them as the Rapid Research Method. It’s the approach I’ve used for many, many projects over many years, and as a way to perform competitive assessments.
What’s important about the techniques is that they make it easy to rapidly organize and share vast amounts of information in an actionable way. Looking back, one of the big surprises for me is how just about any domain can be broken down into questions and tasks. If you know the questions that people ask and the tasks they need to perform, you’ve effectively mapped out the most important information within that domain. This helps you prioritize all the rest of the information, such as concepts, principles, patterns, and practices. Another way to look at it is that all the information is either going to be action or reference. For example, a checklist would be actionable, while a whitepaper on a key topic, tends to be conceptual.
Software, like an information product, tends to suffer from information management problems. It’s tough to share “castles in the mind.” Then there is the people factor. Not everybody can slice and dice information the same way, or with the same skill. The real issue though is sharing “state.” The problem with research is that it’s like climbing a mountain. How quickly can you get others to make it up the mountain, after you? What sort of trail or spikes can you leave along the way? That’s where these research tools that I’m about to share come into play. They help you not only get you and your teammates up the mountain faster, but they leave a trail that others can follow.
Here is the approach in a nutshell:
You can browse the examples below to see what these question lists, task lists, hot spots/frame, and user stories look like.
The Frame is simply a lens for looking at a problem. It’s what’s in the picture and what’s out. How you frame a problem domain can either simplify the problem space, or make it more complex. When you frame the problem space well, it makes it easier to act on it. It makes it easier to identify opportunities for innovation. It makes it easier to research the problem space with better focus. Focus is your friend.
The problem is that you usually don’t know the key areas up front. Framing out the space is part of the challenge and it’s part of the by-product of your research. What I’ve found is that when you start to collect questions and tasks, that “Hot Spots” start to emerge. You will quickly start to see patterns and things will naturally start to cluster. This collection of “Hot Spots” becomes the backbone for your frame. Rather than be complete, it’s about being effective. You can use the 80/20 rule to your advantage here, which is how you both gain speed, but also amplify your impact by focusing on the highest priorities.
Security Frame with Hot Spots
Categories
Architectural Frame Questions List
Contents
Architectural Frame Tasks List
Categories
The beauty is that when you capture the user stories well, it is very easy to deal with both timeless stories and timely ones. In this particular example, even though it’s a few years old, you can see that the top issues that it exposes are alive and well. One additional point on this example is that I used another information pattern. I call it the “View More” pattern. I use it to bubble up the short-list and then push the rest of the list below the “View More …” heading. It’s highly effective for organizing very large information sets, especially if you alphabetize the list.
User Stories for Cloud Enterprise Strategy
Categories


The Rapid Research Method is a way to speed up your product research. It’s also a way to speed up ramp up time when you are leaning a new domain. The Rapid Research Method is also a key for rapid innovation and rapid product design and development. Lastly, the Rapid Research Method is also a great way to map out a space and perform competitive assessments.
One of the challenges with product development is doing effective research for your product design to make sure you have the right map of the pains and needs, the top concerns, and the key desired outcomes. Another challenge is actually making this information actionable and simple to share.
I’ve had the benefit of driving several projects end-to-end, so I’ve been through the research and exploration stage multiple times. I’ve learned a lot of tricks for speeding up research and making it more effective. I’ve had to use these techniques to play catch up in various domains from application architecture to security and performance, to even the cloud. They work.
I’m going to share a few techniques in this post. Collectively, I”ll refer to using them as the Rapid Research Method. It’s the approach I’ve used for many, many projects over many years, and as a way to perform competitive assessments.
What’s important about the techniques is that they make it easy to rapidly organize and share vast amounts of information in an actionable way. Looking back, one of the big surprises for me is how just about any domain can be broken down into questions and tasks. If you know the questions that people ask and the tasks they need to perform, you’ve effectively mapped out the most important information within that domain. This helps you prioritize all the rest of the information, such as concepts, principles, patterns, and practices. Another way to look at it is that all the information is either going to be action or reference. For example, a checklist would be actionable, while a whitepaper on a key topic, tends to be conceptual.
Software, like an information product, tends to suffer from information management problems. It’s tough to share “castles in the mind.” Then there is the people factor. Not everybody can slice and dice information the same way, or with the same skill. The real issue though is sharing “state.” The problem with research is that it’s like climbing a mountain. How quickly can you get others to make it up the mountain, after you? What sort of trail or spikes can you leave along the way? That’s where these research tools that I’m about to share come into play. They help you not only get you and your teammates up the mountain faster, but they leave a trail that others can follow.
About the Approach
The approach is fairly easy. It involves creating simple lists. The power comes from how you create and share these lists. It’s actually the information architecture of the research that unleashes the power of your research. The single best thing you can do with your research is produce output that can easily be used by others, so that you can easily bring in more brains on the problem. When everybody can see the lay of the land, it’s easier for people to find a faster way forward, get resourceful and solve problems.Here is the approach in a nutshell:
- Gather the Questions. In this step, simply start gathering the user questions. Questions are everywhere. The trick is to capture them and put them down on paper. My favorite questions are “Why" and “What is XYZ" and “How does XYZ work” or “When do I use XYZ.”
- Gather the Tasks. In this step, simply gather the user tasks. You can interview users. You can watch them in action. You can survey. You can play and explore the domain yourself. You can analyze search queries. What’s important is that you capture the user actions. This compliments the user questions. Questions are the “conceptual.” Tasks are the “actionable.” When gathering tasks, I find it helpful to write them down individually using the pattern “How To XYZ.”
- Identify the Hot Spots. As you organize your questions list and tasks list into more meaningful buckets, you’ll start to see common categories. Consolidate the categories as best you can. This will help you focus and refine your research and funnel what you learn. These “Hot Spots” will make it a lot easier to slice and dice the domain into actionable nuggets.
- Create a Frame. Use your “Hot Spots” to create a “Frame” for your domain. One way to do this is to create a simple table of your “Hot Spots” and a description of each “Hot Spot.” This creates a quick lens for looking at the domain, and puts a focus on the most important categories of information. When you need to share your research with others, you now have a fast way to show how you broke the information space down and made it more actionable. Experts will quickly validate or correct your frame. That’s the beauty of this approach. You can’t lose. You are always improving it based on what you learn. It’s a true learning system.
- Gather User Stories. User stories are a great way to really take things to the next level. They help to up-level the tasks, build empathy, and really put things in context. I like to manage these as simple lists, and I use the language, “As a user, I want to …”, or “As a user, I need to …”
You can browse the examples below to see what these question lists, task lists, hot spots/frame, and user stories look like.
Key Guidelines to Keep in Mind
- The value of your solution is the value of the problem solved. So the better job you do of capturing the right problems, the better chance you have at a successful product or solution.
- Experience is the short cut. Find the people with experience. You can save yourself exponential time, money, and resources by finding the right people who have the experience who can quickly share the questions, tasks, and scenarios that matter within a given domain.
- Relevancy is king. The best solutions don’t matter if they aren’t relevant. You stay relevant by staying connected. The trick is to stay connected to the key opinion leaders and influencers within a given domain. You want to know the movers and the shakers as well as the folks that play in the domain on a daily basis.
Hot Spots and Frames
“Hot Spots” are simply the key categories or areas of focus. They represent the categories that are key choice points. They are actionable. They are “Hot Spots” because they are 80% of where the action is. They are the 20% of the domain that accounts for 80% of the activity. I use “Hot Spots” as a way to slice a domain down to size and quickly get to what counts. Each “Hot Spots” represents an area that is either a key opportunity or a key pain point. The “Hot Spots” are a great way to organize actionable information such as principles, patterns, and practices.The Frame is simply a lens for looking at a problem. It’s what’s in the picture and what’s out. How you frame a problem domain can either simplify the problem space, or make it more complex. When you frame the problem space well, it makes it easier to act on it. It makes it easier to identify opportunities for innovation. It makes it easier to research the problem space with better focus. Focus is your friend.
The problem is that you usually don’t know the key areas up front. Framing out the space is part of the challenge and it’s part of the by-product of your research. What I’ve found is that when you start to collect questions and tasks, that “Hot Spots” start to emerge. You will quickly start to see patterns and things will naturally start to cluster. This collection of “Hot Spots” becomes the backbone for your frame. Rather than be complete, it’s about being effective. You can use the 80/20 rule to your advantage here, which is how you both gain speed, but also amplify your impact by focusing on the highest priorities.
Frame Example
This is a simple example of a frame using security Hot Spots. By using this collection of Hot Spots, it was very easy to collect questions and tasks within the security domain. It was also easy to walk different technologies and evaluate their security profile. We also used the frame to quickly gather and organize threats, attacks, vulnerabilities, and countermeasures. Organizing the information using this frame made it more actionable, and it made it a lot easier to deal with information overload.Security Frame with Hot Spots
Categories
- Auditing and Logging
- Authentication
- Configuration Management
- Cryptography
- Exception Management
- Input and Data Validation
- Sensitive Data
- Session Management
| Category | Key Considerations |
| Auditing and Logging | Who did what and when? Auditing and logging refer to how your application records security-related events. |
| Authentication | Who are you? Authentication is the process where an entity proves the identity of another entity, typically through credentials, such as a user name and password. |
| Authorization | What can you do? Authorization is how your application provides access controls for resources and operations. |
| Configuration Management | Who does your application run as? Which databases does it connect to? How is your application administered? How are these settings secured? Configuration management refers to how your application handles these operational issues. |
| Cryptography | How are you keeping secrets (confidentiality)? How are you tamper-proofing your data or libraries (integrity)? How are you providing seeds for random values that must be cryptographically strong? Cryptography refers to how your application enforces confidentiality and integrity. |
| Exception Management | When a method call in your application fails, what does your application do? How much do you reveal? Do you return friendly error information to end users? Do you pass valuable exception information back to the caller? Does your application fail gracefully? |
| Input and Data Validation | How do you know that the input your application receives is valid and safe? Input validation refers to how your application filters, scrubs, or rejects input before additional processing. Consider constraining input through entry points and encoding output through exit points. Do you trust data from sources such as databases and file shares? |
| Sensitive Data | How does your application handle sensitive data? Sensitive data refers to how your application handles any data that must be protected either in memory, over the network, or in persistent stores. |
| Session Management | How does your application handle and protect user sessions? A session refers to a series of related interactions between a user and your Web application. |
Question List Example
A “Question List” is simply a list of the key questions that people ask. You can find the key questions through surveys, going through forums, looking through blogs, and through hands on experience. Hands on experience helps you build empathy for what really matters, which will be essential when you are trying to rank, rate, and sort your list. It also helps to organize your questions into “Hot Spot” areas or buckets.Architectural Frame Questions List
Contents
- Authentication and Authorization
- Caching and State
- Communication
- Composition
- Concurrency and Transactions
- Configuration Management
- Coupling and Cohesion
- Data Access
- Exception Management
- Logging and Instrumentation
- User Experience
- Validation
- Workflow
- What are the approaches for identity store?
- What authentication mechanism will be used?
- What are relevant authentication and authorization patterns?
- How do I decide if I need to implement single sign-on?
- How do I design frontend single sign-on?
- How do I design for backend single sign-on?
- How to I flow identity to backend?
- What is impersonation and when should I use it?
- What is delegation and constrained delegation?
- How do you refresh your cache?
- How to design effective caching mechanism?
- What are common architectural pitfalls with caching?
- Which layers should implement caching?
- What data should be cached? (presentation, business and data access layers)
- How to choose a cache be store?
- How to cache data with different logical scopes?
- How to cache data on client side?
- How to cache user specific data?
- How to decide whether caching data will improve performance?
- How to manage expiration policy and scavenging mechanism?
- How do I protect cached data?
- How do I structure my application to optimize communication efficiency?
- How do I protect my communication channels?
- How do I choose appropriate communication protocol?
- How to flow identity across layers (tiers)?
- What are the common architectural pitfalls with communication?
- How do I structure my application to optimize communication efficiency?
- How do I protect my communication channels?
- How do I choose appropriate communication protocol?
- How to flow identity across layers (tiers)?
- What are the common architectural pitfalls with communication?
- What are effective techniques for communication between the tiers?
- What are effective techniques for exchanging data between the tiers?
- How to secure communication between the layers?
- When should I use synchronous communication?
- When should I use asynchronous communication?
- What are effective transaction management strategies?
- How do I determine concurrency requirements?
- What are the common architectural pitfalls with transactions?
- What’s the right level of granularity of transactions?
- How do I manage distributed transactions?
- What are the common architectural pitfalls with concurrency?
- How do I manage per app configuration?
- How do I manage per user configuration?
- How do I synchronize configuration across distributed environment (solutions)
- What are the effective configuration management patterns?
- What are the common architectural pitfalls with configuration?
- How to determine effective layering strategy?
- What are effective design patterns for coupling and cohesion?
- How to determine appropriate coupling between components and between layers?
- What are the common architectural pitfalls with coupling and cohesion?
- How do we pass data through the layers (tiers)?
- How to design effective data abstraction layer?
- How to model the data?
- How to page records?
- How to design for very large databases?
- What are the common architectural pitfalls with data access?
- What is domain-driven architecture?
- What is a database-driven architecture?
- How do I choose between domain-driven and database-driven?
- Which technology should be used to access data store?
- How to manage database connections?
- What logic should be implemented in the data helper components?
- How to handle transactions?
- How to handle concurrency?
- How to design for a multi-tenant database?
- How to choose between in-line SQL and Stored Procedures?
- How to design effective exception management strategy?
- What are effective exception management patterns?
- What are the common architectural pitfalls with exception management?
- How to design effective exception management strategy?
- What are effective exception management patterns?
- What are the common architectural pitfalls with exception management?
- Whether to design custom exception handling logic?
- Which layers should implement exception management?
- How to deal with unhandled exceptions?
- How to display exception info to users?
- How to design logging of exception data?
- How to propagate exceptions through layers?
- How to design effective layering strategy?
- What are effective design patterns for layering?
- How to separate layers into areas of concerns?
- How should layers interact?
- What are the common architectural pitfalls with layering?
- How to design effective layering strategy?
- What are effective design patterns for layering?
- How to separate layers into areas of concerns?
- How should layers interact?
- What are the common architectural pitfalls with layering?
- How do I migrate my existing architecture to layered architecture, for example monolithic to layered architecture, from 2-tier to layered architecture or 3-tier to layered architecture?
- How should I structure my development teams i.e. group by layers or group by functional modules?
- How will my solution and project structure look like when using Layered Architecture?
- How to design effective logging and instrumentation strategy?
- What are effective logging and instrumentation patterns?
- What are the common architectural pitfalls with logging and instrumentation?
- How to design effective logging and instrumentation strategy?
- What are effective logging and instrumentation patterns?
- What are the common architectural pitfalls with logging and instrumentation?
- Which layers should implement logging?
- When do I need a custom logging mechanism?
- How to make logging configurable?
- How to secure of logged data?
- How to design effective State Management?
- What are common architectural pitfalls with state management?
- Which components should be stateful?
- Which components should be stateless?
- Where should I store state?
- What information should be cached?
- How to manage state in a web farm?
- How to protect state data?
- What are the effective strategies and patterns for structuring the applications?
- How do I divide the application into sub-system?
- How do I factor the applications into layers, components and services?
- How do I factor the application into tiers?
- What are the common architectural pitfalls with Structuring?
- What are the effective strategies and patterns for structuring the applications?
- How do I divide the application into sub-system?
- How do I factor the applications into layers, components and services?
- How do I factor the application into tiers?
- What are the common architectural pitfalls with Structuring?
- Where do you perform validation?
- What do you validate?
- How to validate business rules?
- How to protect against malicious data?
- How to handle data validation exception?
- What are the common architectural pitfalls with validations?
- How to design client side validation?
- How to determine trust boundary for validation?
- What are the different types of workflows? What are the differences between them?
- What are common workflow scenarios?
- What are effective workflow patterns?
- What are effective the tools for designing workflow?
- What is workflow modeling and how does it help in system design?
- What are the common pitfalls with using workflows?
- What is “workflow persistence”?
- How does workflow communicate with the system?
- How design for error recovery in a workflow?
- How do I manage workflow instances?
- How do I host workflows?
Task List Example
A “Task List” is simply a list of the tasks that users perform within a domain. I find it helpful to use the language “How To.” This forces people to think in terms of goals. Sometimes it’s helpful to know the goal. Sometimes it’s more helpful to know the specific tasks. When you need to up-level it, simply ask “What are you trying to accomplish?” When you need to drop down a notch, simply ask, “What are you trying to do?” You can collect tasks from users through interviews, surveys, etc. Again, I find that hands-on is one of the best ways to really build empathy for the pains and needs. The real power comes from transforming from the problem side (the pains and needs), to the solution side (the specific goal or task that would address the pain or need.)Architectural Frame Tasks List
Categories
- Authentication and Authorization
- Caching and State
- Communication
- Composition
- Concurrency and Transactions
- Configuration Management
- Coupling and Cohesion
- Data Access
- Exception Management
- Logging and Instrumentation
- User Experience
- Validation
- Workflow
- How to identify trust boundaries
- How to design single sign-on strategy
- How to design role-based authorization
- How to design resource-based authorization
- How to design claims-based authorization
- How to design a trusted sub-system
- How to flow identity across layers and tiers
- How to improve performance with caching
- How to decide what data to cache
- How to decide where to cache data
- How to cache data on client side
- How to cache user specific data
- How to manage expiration policy and scavenging mechanism
- How to protect cached data
- How to implement thread safety for the cached items using locking
- How to cache data proactively
- How to cache data reactively
- How to design caching for distributed environment
- How to design caching for web farm scenarios
- How to structure an application to optimize communication efficiency
- How to design for remote communication
- How to protect communication channels
- How to choose a communication protocol
- How to pass data across layers
- How to flow identity across layers (tiers)
- How to secure communication between the layers
- How to design for synchronous communication
- How to design for asynchronous communication
- How to design fire and forget (one way) communication
- How to design for transactions
- How to manage distributed transactions
- How to design for atomic transactions
- How to design for long running transactions
- How to design for distributed transactions
- How to choose isolation level
- How to design configuration
- How to choose for configuration store
- How to separate application data from configuration data
- How to synchronize configuration across distributed environment
- How to protective sensitive configuration information
- How to enable changing configuration information at run-time
- How to design for loose coupling across layers
- How to design for high cohesion within layers
- How to design message based interfaces
- How to design your data access layer
- How to design data abstraction
- How to pass data across layers and tiers
- How to model your data
- How to page records
- How to design for very large databases
- How to design a domain-driven architecture
- How to design a database-driven architecture
- How to manage database connections
- How to handle transactions
- How to handle concurrency
- How to design for a multi-tenant database
- How to design exception management
- How to design for unhandled exceptions
- How to design structured exception handling
- How to design for appropriate display of exception data
- How to plan and design for exception logging
- How to propagate exceptions in a distributed design
- How to design for notifications
- How to design layering
- How to choose communication options between layers
- How to design message based interfaces for remove layers
- How to separate layers into areas of concerns
- How to design logging
- How to design for instrumentation
- How to design logging for distributed environment
- How to design logging for web farm scenario
- How to configure logging
- How to secure logged data
- How to choose the appropriate state model
- How to flow call context data across application layers
- How to design State Management
- How to store state
- How to manage state in a web farm
- How to protect state data
- How to design for passing data across tiers
- How to choose patterns for structuring your application
- How to factor security requirements when structuring your application
- How to factor performance and scalability requirements when structuring your application
- How to factor the applications into layers, components and services
- How to factor the application into tiers
- How to identify trust boundaries
- How to design a centralized validation solution
- How to validate input and data against business rules
- How to validate input and data for security
- How to validate the integrity of data
- How to handle data validation exceptions
- How to design workflow
- How to choose a workflow technology
- How to choose authoring mode
Summarizing Task Lists
I’ve found it especially helpful to organize massive lists of tasks into simple two-column tables. This creates a nice view that makes it very easy to prioritize, cut, or elaborate, in a fast and simple way. You can color code your lists. You can bubble key things to the top. You can make whitespace where you need it. You can group your tasks under sub-items within a row. The choices are endless, but the two-column tables does make dealing with massive mounds of information a breeze. The way it compacts and frames information makes scanning very easy, which is important when you are trying to get the “bird’s-eye view.”| Category | Items |
| Authentication and Authorization | |
| Caching | Design
|
| Communication |
|
| Concurrency and Transactions |
|
| Configuration Management |
|
| Coupling and Cohesion |
|
| Data Access | Design
|
| Exception Management |
|
| Layering |
|
| Logging and Instrumentation |
|
| State Management |
|
| Structure |
|
| Validation |
|
| Workflow |
|
User Stories at a Glance Example
One of the most powerful techniques I use to rapidly gather user requirements is user stories. I find that capturing user stories with the language, “As a user, I need to” .. or “As a user, I want to …” really helps add context and clarity, while keeping it amazingly simple. I also find that organizing the user stories by Hot Spots helps go a long way, especially when you are dealing with a large amount of information. Below is an example where I was collecting user stories to rapidly figure out the top concerns of business leaders and Enterprise Architects when it comes to cloud computing.The beauty is that when you capture the user stories well, it is very easy to deal with both timeless stories and timely ones. In this particular example, even though it’s a few years old, you can see that the top issues that it exposes are alive and well. One additional point on this example is that I used another information pattern. I call it the “View More” pattern. I use it to bubble up the short-list and then push the rest of the list below the “View More …” heading. It’s highly effective for organizing very large information sets, especially if you alphabetize the list.
User Stories for Cloud Enterprise Strategy
Categories
- Awareness / Education
- Architecture
- Availability
- Competition
- Cost
- Governance and Regulation
- Industry
- Integration
- Operations
- People
- Performance
- Planning
- Risk
- Security
- Service Levels / Quality of Service
- Solutions
- Sourcing
- Strategy
- Support
| Category | Items |
| Awareness / Education |
View More…
|
| Architecture |
View More…
|
| Availability |
View More…
|
| Competition |
|
| Cost |
View More…
|
| Governance and Regulation |
View More…
|
| Industry |
|
| Integration |
|
| Operations |
View More…
|
| People |
View More…
|
| Performance |
View More…
|
| Planning |
View More…
|
| Risk |
View More…
|
| Security |
View More…
|
| Service Levels / Quality of Service |
View More…
|
| Solutions |
View More…
|
| Sourcing |
|
| Strategy |
|
| Support |
View More…
|
Subscribe to:
Posts (Atom)


